DawgCTF 2022
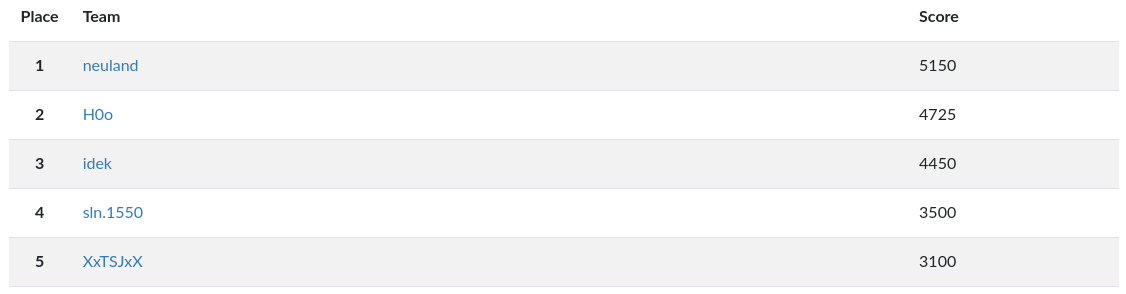
We (neuland) participated at the DawgCTF 2022. We even got first place :)
This post highlight some challenges and their writeups.
Hiding in Plain Sight - 50 points
Description: I think someone hid a message in this picture. Can you EXtract it?
We get a .jpg file. If we look at the image we can se a string in the top left corner. The string is a base58 decoded string of a part of the flag. Next, we run exiftool on the file to get additional information. Within the Subject contains a binary string that can be translated to another part of the flag. Same goes with Author and Comment. Both are encoded.
Flag: DawgCTF{y0U_C4n'7_h!D3_fR0M_m3}
Hivemind - 100 points
Description: What kind of web server is the hivemind hosting?
We get a large file that show a dump of a Windows registry hive. We are able to find one web server that is xampp within the file. The entry contains a Location key that was changed afterwards (we installed xampp to see what kind of registry keys were created) and shows some hex-data. Now we need to decode the string:
- Convert string from hexadecimal
- Decode from base58
- ROT13
Flag: DawgCTF{7h3_h!v3_m!nd_83(k0n5}
Glenda’s Revenge - 125 points
Description: We got a packet capture from this really pretentious dude in New Jersey. Can you get the flag out of it?
We get a .pcapng file that shows that a protocol with the name Plan 9 is used. It turns out that this protocol is pretty old and from Bell Labs. If we filter for data transmitted within the protocol (data as a filter in Wireshark) we can see that some files are opened. Including a file called flag.txt. If we follow the TCP stream we can even see the content of the files. The file contains the string RGF3Z0NURntpdHNfbjB0X2FfdW5peF9zeXN0M21faV9kMG50X2tuMHdfdGgxc30K. This is a base64 encoded string of the flag.
Flag: DawgCTF{its_n0t_a_unix_syst3m_i_d0nt_kn0w_th1s}
Allium Cepa - 150 points
Description: “You’re so wrapped up in layers onion boy, you’re afraid of your own feelings.” Can you get to the core?
We get a .pdf file that shows Shrek the ogre but nothing more.
First, we run binwalk on the downloaded .pdf file. Binwalk detect different files. On is pretty interesting. On my system, the file is called 21A7B and it is a Zip archive data, at least v2.0 to extract. If we binwalk the file again, we will find a powershell file (.ps1). The file is not that interesting. It includes some calls and a big string. This string can be decoded to another file (.png) what shows the flag.
Flag: DawgCTF{09r35_4r3_1!k3_0n!0n5}